Centralized Security Management: Effective Operating Principles and the Role of SOC

Discover centralized security management: Operating principles, benefits compared to decentralized models, and the pivotal role of SOC (NetGuardX) in comprehensive enterprise protection.
How Does a Centralized Security Management System Work?
A centralized security management system operates on the principle of unified control and monitoring. Unlike decentralized methods where local teams make security decisions independently, centralized network security management establishes consistent standards and protocols across the entire organization.
Centralized models provide focused oversight and consistency, whereas decentralized models allow for rapid autonomy at the group level. Key differences include control authority, scalability, policy enforcement, and compliance capabilities.
This system integrates multiple security functions, including threat detection, incident response, compliance management, and policy enforcement onto a unified platform. The result is a more effective and tightly coordinated defense strategy capable of adapting quickly to emerging threats.
The centralized security management model helps enterprises establish unified and consistent control across the entire system.
Key Components and Functions
- Centralized Monitoring (Single-Pane-of-Glass): Provides a comprehensive view of every tool, eliminating blind spots and helping identify threats faster.
- Security Policy Enforcement: Ensures consistent application of security standards across all devices and environments, preventing configuration drift.
- Role-Based Access Control (RBAC): Assigns detailed permissions according to hierarchy and responsibility, minimizing security risks.
- Comprehensive and Unified Visibility: Delivers contextual information regarding security events and system performance across the entire infrastructure.
How Centralized Security Management Operates?
Instead of managing a patchwork system of disjointed firewalls, antivirus software, and intrusion detection systems (IDS), the centralized model offers a comprehensive view and a unified control point.
- Integration with Existing IT Infrastructure: A robust centralized management system can collect data from and push policies to a wide array of security tools, ranging from endpoint protection to network firewalls. This helps eliminate security fragmentation and creates a stronger defense layer.
- Automation and Orchestration: Once all tools connect, the system can automate repetitive tasks and orchestrate complex responses to threats. For example, if the system detects a vulnerability on a device, it can automatically isolate that device and restrict network access via NAC (Network Access Control) policies.
Deployment Methods
CMS (Centralized Management System)
A CMS provides a dashboard to monitor and manage devices as well as security policies from a central location. This serves as the "brain" that connects and controls all other security components. A robust CMS can collect data from and push policies to a multitude of security tools, from endpoint protection to centralized firewall management across network segments.
Cloud Security Management
This method leverages flexible and scalable infrastructure to provide centralized monitoring capabilities across distributed environments, including on-premise, hybrid cloud, and multi-cloud. This approach is particularly suitable for organizations with remote workforces or those utilizing multiple cloud platforms, ensuring the ability to collect, analyze, and process data securely and effectively.
SOC (Security Operations Center)
The SOC is a dedicated team and facility responsible for monitoring, detecting, and responding to cybersecurity incidents. While systems like CMS provide the technology and data platform, the SOC plays a pivotal role with the human element. It comprises analysts capable of evaluating context, processing alerts, conducting deep investigations, and optimizing security policies in real time.
SIEM (Security Information and Event Management)
SIEM solutions collect, aggregate, and analyze security data from various sources (firewalls, servers, applications, endpoints, etc.) to provide a panoramic, real-time view of cybersecurity status. This is the core component that helps detect abnormal behaviors early, generates accurate alerts, and effectively guides the response actions of the SOC team.
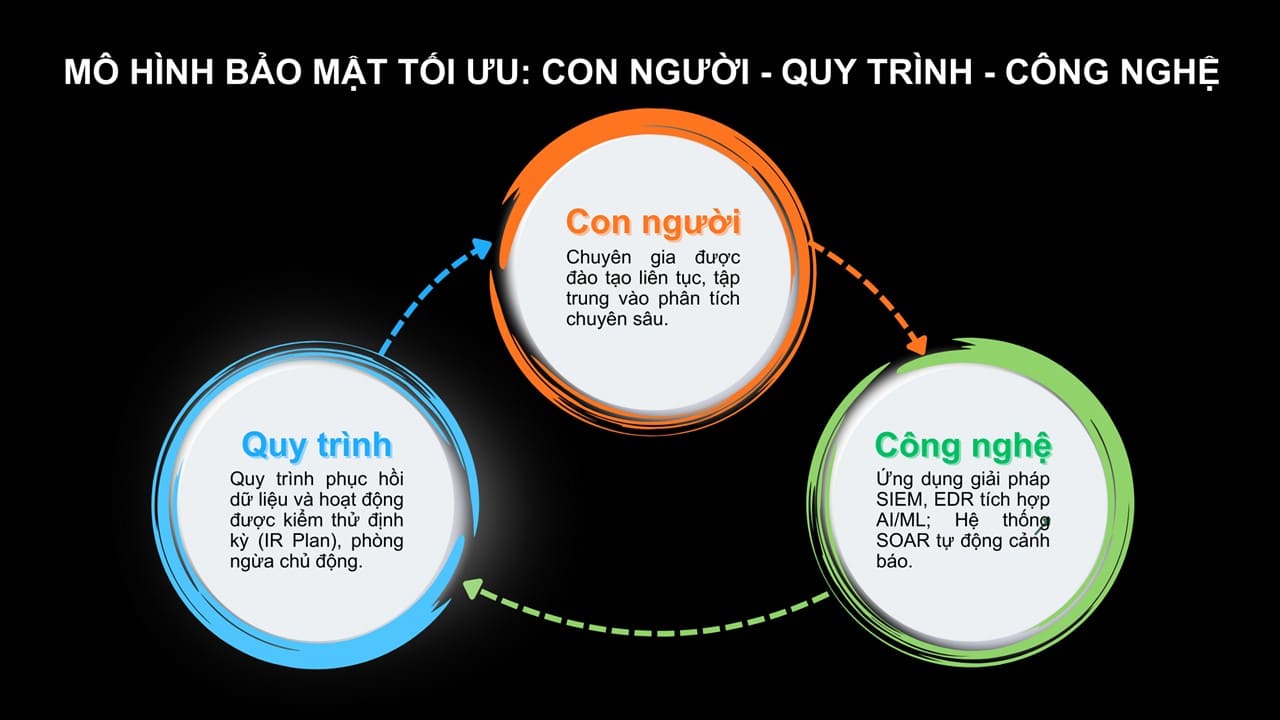
The Security Operations Center (SOC) combines the power of SIEM technology and expert analysts for 24/7 monitoring
Unified Security Platform
As data and infrastructure become increasingly distributed globally, a centralized and unified security management solution is an effective way to ensure security and consistent control. By replacing disjointed tools with a centralized management platform, organizations minimize operating costs, avoid maintenance duplication, reduce misconfiguration risks, and simultaneously enhance protection efficiency.
However, modern unified security platforms do more than just consolidate tools; they provide comprehensive, multi-layered protection across every attack vector. These platforms integrate real-time threat intelligence to counter zero-day exploits, ransomware, and targeted attacks. They also expand protection scope from endpoints and file transfers to the hardware supply chain, portable storage devices, and file-based attack vectors.
Advanced platforms utilize CDR (Content Disarm and Reconstruction) technology and multi-engine scanning to neutralize threats hidden within files without disrupting workflows, while enforcing compliance policies and Zero Trust access. Through centralized management, administrators deploy consistent rules across cloud and on-premises environments, significantly reducing misconfigurations and systematically closing attack vectors before they can compromise critical infrastructure.
Benefits of Centralized Security Management
Policy Enforcement and Access Management
Effective centralized access control systems implement sophisticated permission structures, helping balance security requirements with operational needs. These systems support complex organizational structures while maintaining strict security boundaries.
Integrated Access Control mechanisms orchestrate privileges across multiple systems and applications. With RBAC (Role-Based Access Control), organizations can define a role once and apply it consistently across all systems, minimizing administrative burden and security risks. This approach reduces security threats while maintaining operational efficiency, especially when managing diverse endpoint environments across the organization.
Unified Monitoring and Incident Response
Centralized monitoring capabilities completely change how organizations detect and respond to security threats. By aggregating data from multiple sources, these systems identify patterns and anomalies that individual monitoring tools might miss.
Automated Incident Response processes reduce response time and ensure consistent handling of security events. The system can automatically isolate affected devices, collect forensic data, and trigger recovery procedures.
Integration with a Defense in Depth strategy provides multiple tightly coordinated protection layers. Centralized management ensures every security layer works effectively together rather than operating in isolation.
Centralized vs. Decentralized Security Management
|
Criteria |
Centralized Management |
Decentralized Management |
|
Policy Consistency |
High |
Inconsistent (Variable) |
|
Response Speed |
Medium (requires coordination/orchestration) |
Fast (local/on-site decision making) |
|
Resource Efficiency |
High (shared resources and expertise) |
Lower (duplicated resources and expertise) |
|
Scalability |
Excellent (based on centralized infrastructure) |
Limited (dependent on local resources) |
|
Compliance Management |
Simplified (Unified, centralized reporting system) |
Complex (multiple control points require compliance) |
|
Implementation Cost |
Higher initial capital investment |
Lower initial cost per unit |
|
Visibility |
Comprehensive across the entire organization |
Limited to local scope |
|
Flexibility |
Lower (standardized methods) |
Higher (customized solutions) |
How to Deploy Centralized Security Management: Best Practices
Managing and Automating Security Policies
Effective policy management creates a balance between security requirements and operational efficiency. Automated policy updates ensure consistent enforcement while reducing administrative burdens.
Automating security policies allows organizations to react quickly to new threats and regulatory changes. Automated systems can deploy policy updates across the entire infrastructure simultaneously.
Ensuring consistent enforcement across different environments requires careful attention to configuration management and policy translation. Centralized systems must account for environmental differences while maintaining security standards.
Integration with Compliance Standards
- Regulatory Alignment: Provide a comprehensive overview of all managed endpoints, highlighting compliance levels with key industry standards such as NIST, GDPR, CISA, HIPAA, and ISO 27001.
- Streamlined Reporting: Use centralized dashboards to generate audit-ready reports immediately.
NetGuardX - SOC Service Towards Centralized Security Management
In a landscape where cyber threats become increasingly sophisticated and IT systems become distributed, maintaining disjointed security tools is no longer sufficient to ensure safety. NetGuardX – NetNam's Security Operations Center as a Service (SOCaaS) is the answer to the centralized security management problem, helping enterprises shift from a passive stance to proactive defense.
NetGuardX is not merely a monitoring tool but a unified security ecosystem where people, processes, and technology converge to protect the enterprise's digital assets 24/7.
Why is NetGuardX the Optimal Choice for a Centralized Management Strategy?
- Unified Visibility: Collects and standardizes data from all sources (Firewall, Endpoint, Cloud) onto a single Dashboard thanks to Single-Pane-of-Glass monitoring, completely eliminating monitoring blind spots.
- Power of AI & Automation: Integrates AI/Machine Learning and EDR/NDR to automatically detect abnormal behaviors and trigger rapid responses, maximizing the reduction of Mean Time to Resolve (MTTR).
- Standard Compliance: Operates according to NIST standards and meets legal regulations (such as Decree 13/2023/ND-CP), supporting easy extraction of centralized audit reports.
- Cost & Resource Optimization: The SOC-as-a-Service model acts as an "extended security department," providing a team of experts on duty 24/7 without the costs of hardware investment or personnel training.
Ready to Elevate Your Security System?
Do not let disjointed management become a vulnerability for hackers to exploit. Let NetGuardX establish a centralized, intelligent, and solid "shield" today.
Contact NetNam immediately for consultation on the most suitable SOC strategy for your enterprise!
Contact NetNam:
- Hotline: 1900 1586
- Email: netguardx@netnam.vn
- Website: www.netnam.com
- Comprehensive Cybersecurity Monitoring Service www.netguardx.netnam.com
Submit your request








